Introduction
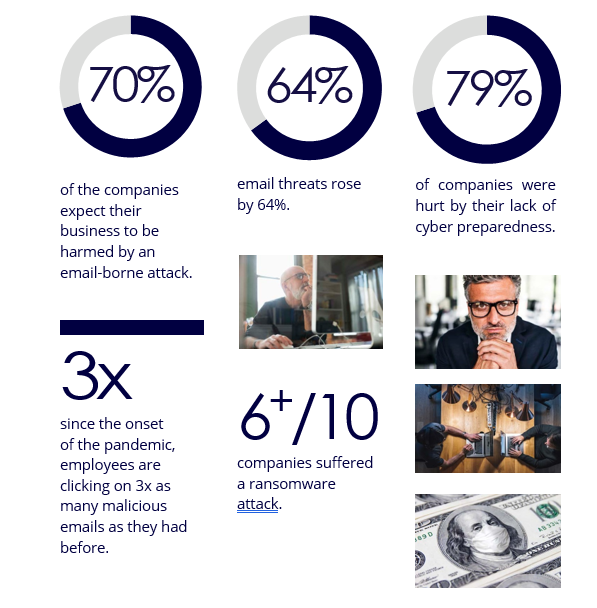
Email remains the most important tool of communication in the modern business world. Every day, billions of emails are sent between computers, phones, and tablets. This includes both corporate email platforms and cloud-based email platforms for personal use. Due to its widespread use, it is considered the number one threat vector. As the use of e-mail grows, so the threats to e-mail grow. Due to the COVID-19 pandemic, workplaces have been moved from offices to homes. This situation caused the growth of email threats and actualizes to take urgent effective actions for threat protection. If look at the infographic below, we can see how dangerous the situation with email threats is. This situation reflects the threats to email systems associated with the COVID-19 pandemic over the last 12 months (1):
Problems
Cybercriminals, of course, are moving forward and creating new and creative threat methods. Email threats pose significant challenges for both corporate and individual email users. For example, we can list these problems as below:
- Email threats can result in significant financial losses and waste of time;
- Business email compromise causes serious financial and reputational losses;
- The use of email systems in ransomware attacks poses serious threats to both corporate and individual users
- Domains are compromised and used by spam and phishing campaigns via email systems
- Cybercriminals use emails to perform malware propagation. Information is then intercepted through these malicious programs, and users unknowingly participate in various malicious campaigns of cybercriminals.
- The phishing method is used for data disruption and user data theft, and the mail systems are the main tool here.
- There is a need for new protection approaches and methods as users move to Cloud email systems.
All of the problems we have listed are of concern to corporate and individual users, and these problems lead to serious financial and, ultimately, loss of reputation leading to financial loss.
Approach to problem solving
Given the complexity of the problems, it is clear that they cannot be solved with a simple approach. Because each problem occurs at different levels due to the use of different methods by attackers. But the platform where the problems arise is the email system. Therefore, a more comprehensive and layered approach to problem solving is needed. Every company that today uses an e-mail system as an active tool of communication and has a corporate e-mail user believes that a protection system that must deal with threats from e-mail systems should have at least the following features:
- Malware protection
- Should be able to encrypt data
- Should be able to protect against phishing attacks
- Should be able to securely authenticate email users
- Should be possible continuous monitoring
- Should be able to receive feed from Threat Intelligence for proactive protection.
- Should be able to prevent data leakage from companies over email
- Both on-premises and cloud-based mail systems should be protected
- The solution vendor should be able to provide high-quality technical support
- The system integrator implementing the solution must have experience in implementing the solution and appropriate qualified engineers
Email security solution that meets all these requirements can be considered more reliable and can minimize the risks associated with email threats.
Solution
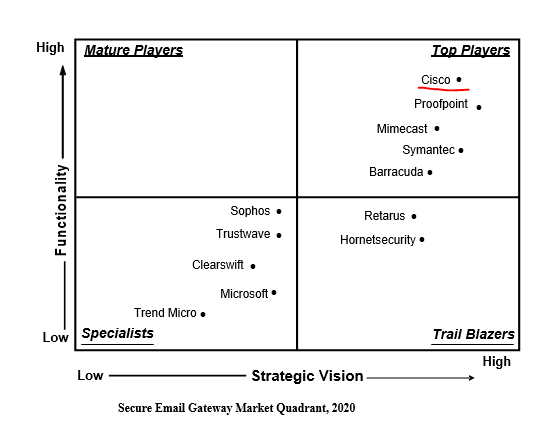
Today, in the global IT market, there are many manufacturing companies offering solutions for protecting e-mail systems(2). As a result of our research, we chose the CISCO Secure Email solution. Secure Email solution capabilities that can address these challenges, leadership in the Gartner Quadrant(3), BESTCOMPGROUP’s longstanding partnership with CISCO, and experienced engineers for CISCO products played an important role in our selection.
If any solution is required to provide better protection, it is essential that the solution have a Threat Intelligence platform or be able to integrate to it. The Secure Email solution enhances protection by integrating with CISCO’s Talos Threat Intelligence platform. Talos analyzes global Internet traffic 24 hours a day. Thus, 600 billion e-mail, 16 billion web requests and 1.5 mln. malware samples are analyzed per day by Talos. As a result, it detects new threats and anomalies and creates updates based on this information. These updates are sent to Secure Email every 3-5 minutes and provide email security against 0-day or 0-hour attacks..
Secure Email uses two types of filtering mechanisms to prevent against spam. These are filtering mechanisms based on external factors, i.e. IP address and reputation, as well as in-depth analysis of internal email. Reputation filtering is based on Talos Threat Intelligence platform feed and can prevent up to 90% of spam to users(4).
Graymail is a letter used to send newsletters, advertisements and promotional information. While these types of emails are useful to some users depending on their industry and job title, some users perceive such emails as spam and do not want to receive them. These messages usually contain an unsubscribe link that the user can unsubscribe from by clicking on this link. Cybercriminals successfully use this in their phishing campaigns by hiding malicious links under these links. Secure Email can detect these malicious links and safely unsubscribe.
Secure Email uses Talos Threat Intelligence data and antivirus data from various vendors to protect against known viruses and zero-day viruses. Secure Email can also provide very effective protection against unknown zero-day malicious files as well as complex polymorphic threats with the CISCO AMP (Anti-Malware Protection) product. It is able to detect malicious files using signatures, neutralize more complex polymorphic threats using FuzzyFingerprinting and machine learning.
Cisco Secure Email can detect and prevent phishing and forged emails using DNS-based DMARC, DKIM, and SPF methods. The CAPP (Cisco Advanced Phishing Protection) service in this solution prevents attacks such as social media, BEC (Business Email Compromise), and impostors designed to trick users. It uses both local email intelligence and machine learning to simulate trusted mail behavior and provide security based on this simulation.
Almost all users are starting to migrate to cloud-based email platforms. One of the most popular of these platforms is the Microsoft O365 platform. While the platform itself provides some security measures, customers always need more and require a deeper secure solution. The Cisco Secure Email solution integrates with the Microsoft O365 platform to provide effective security like for on-premises email platforms.
The fact that our confidential and very sensitive information leaves our network and falls into the wrong hands does not bode well for our company. Even if this happens, it is necessary to make it impossible to read and use this information using encryption. To prevent this, CISCO Secure Email offers proprietary DLP (Data Loss Prevention) and CRES (Cisco Registered Envelope Service) encryption services.
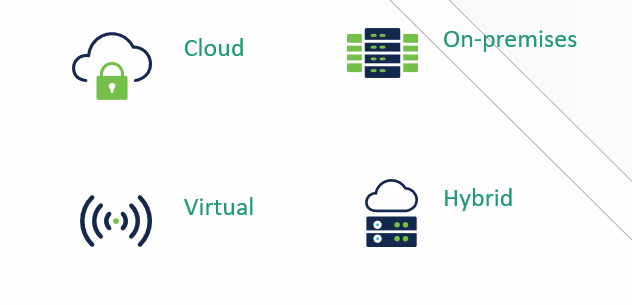
Cisco Email Security has different deployment options(4). You can choose any option depending on your requirements.
There is a hybrid deployment. This is an interesting approach. This approach can be used in a variety of situations. For example, you can use the Cloud option for incoming emails, and you can set up a local system for outgoing emails. Or, if you plan to gradually migrate to the cloud, you can install both products at the same time and gradually migrate completely to the cloud without compromising security.
Technical Support
BESTCOMP GORUP has engineers who have been trained in the implementation of CISCO solutions, as well as Cisco Secure Email solutions, have passed exams and received certificates and have successfully implemented these solutions for customers. At the same time, CISCO has a large knowledgebase, provides 24/7 technical support, professional service and timely software updates.
Conclusion
With the ever-growing cyber threats and the significant proportion of email threats(5) among these cyber threats, we, as BESTCOMP GROUP, have included Cisco Secure Email in our portfolio to help keep our customers safe. The Cisco Secure Email solution allows to prevent threats such as BEC, ransomware, sophisticated malware, phishing, spam, data loss, and more with its features, capabilities and services. Technical support provided by CISCO and BESTCOMP companies adds value to the Cisco Secure Email solution.
References
- https://www.mimecast.com/globalassets/documents/ebook/state-of-email-security-report-2021.pdf
- https://www.gartner.com/reviews/market/email-security
- https://www.cisco.com/c/dam/en/us/products/collateral/security/secure-email-gateway-market.pdf
- https://www.cisco.com/c/en/us/products/collateral/security/cloud-email-security/datasheet-c78-742868.html
- https://www.securitymagazine.com/articles/90345-more-than-three-billion-fake-emails-are-sent-worldwide-every-day
Author: Mammad Mammadov